GitLab Runner Deployment and Testing
Images and Software
The following table lists the images required during installation. The version numbers are for reference only.
| Image | Version |
|---|---|
| gitlab/gitlab-runner | alpine-v14.4.0 |
| gitlab/gitlab-runner-helper | x86_64-54944146 |
If the Internet is unavailable in the environment, download the required images in advance. Download the images from the Docker Hub official website https://hub.docker.com.
Using gitlab-runner.yaml to Start the Runner Container
In the gitlab-runner.yaml file, change the image name. The following is an example of the .yaml file. Modify the file as required.
vim gitlab-runner.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: gitlab-runner
namespace: default
spec:
replicas: 1
selector:
matchLabels:
name: gitlab-runner
template:
metadata:
labels:
name: gitlab-runner
spec:
containers:
- args:
- run
image: gitlab/gitlab-runner:alpine-v14.4.0
imagePullPolicy: IfNotPresent
name: gitlab-runner
volumeMounts:
- mountPath: /etc/gitlab-runner
name: config
readOnly: false
- mountPath: /etc/ssl/certs
name: cacerts
readOnly: true
restartPolicy: Always
volumes:
- hostPath:
path: /etc/gitlab-runner
name: config
- hostPath:
path: /etc/ssl/key
name: cacerts
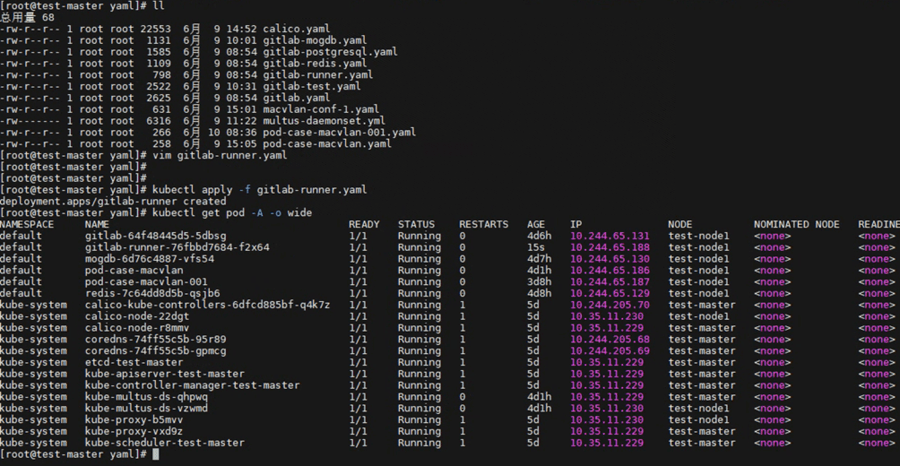
Start the container.
# kubectl apply -f gitlab-runner.yaml
# kubectl get pod -A -o wide
Creating a Container Project That Uses User Certificates for Authentication in GitLab
Click New project.
Select Create blank project.
Enter a name for the project.
Choose Settings > CI/CD > Runners > Expand.
Record the address and token for registering the Runner.
Import certificate files.
Check and generate certificate files admin.crt, admin.key, and ca.crt on the master node.
View certificate information.
# cat /etc/kubernetes/admin.conf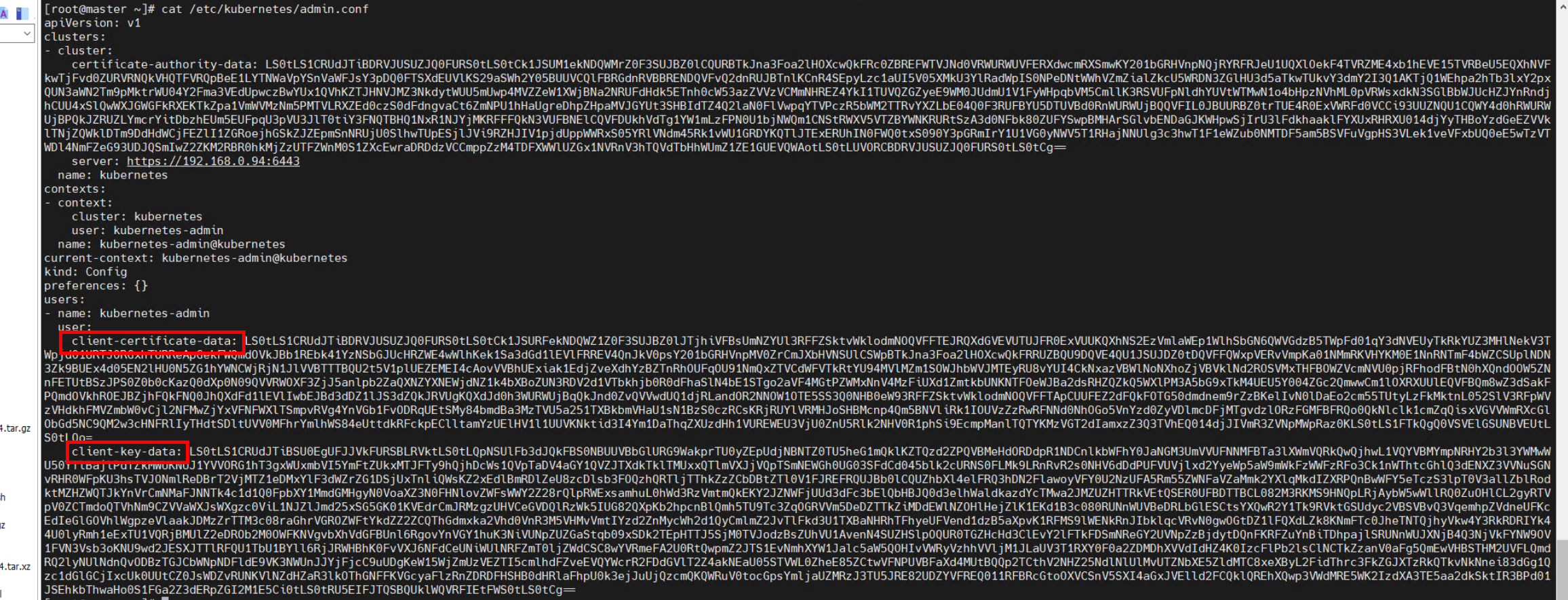
Generate the encrypted admin.crt.
# echo "${client-certificate-data}" | base64 -d > admin.crtGenerate the encrypted admin.key.
# echo "${client-key-data}" | base64 -d > admin.keyObtain the CA certificate on the manager node.
# cp /etc/kubernetes/pki/ca.crt ./
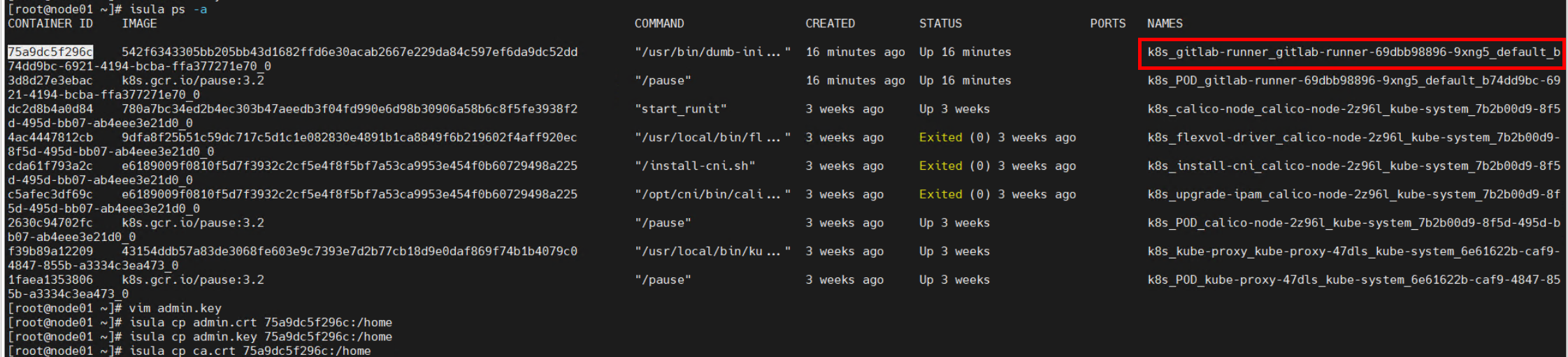
Import the three certificate files to the GitLab Runner container on the node where the Runner is running.
Note: To import the certificate files, check the node where the GitLab Runner is running, copy the certificate files to the node, and run the isula cp command to import the certificate files.
# isula cp admin.crt [Container ID]:Storage path # isula cp admin.key [Container ID]:Storage path # isula cp ca.crt [Container ID]:Storage pathNote: The isula cp command can copy only one file at a time.
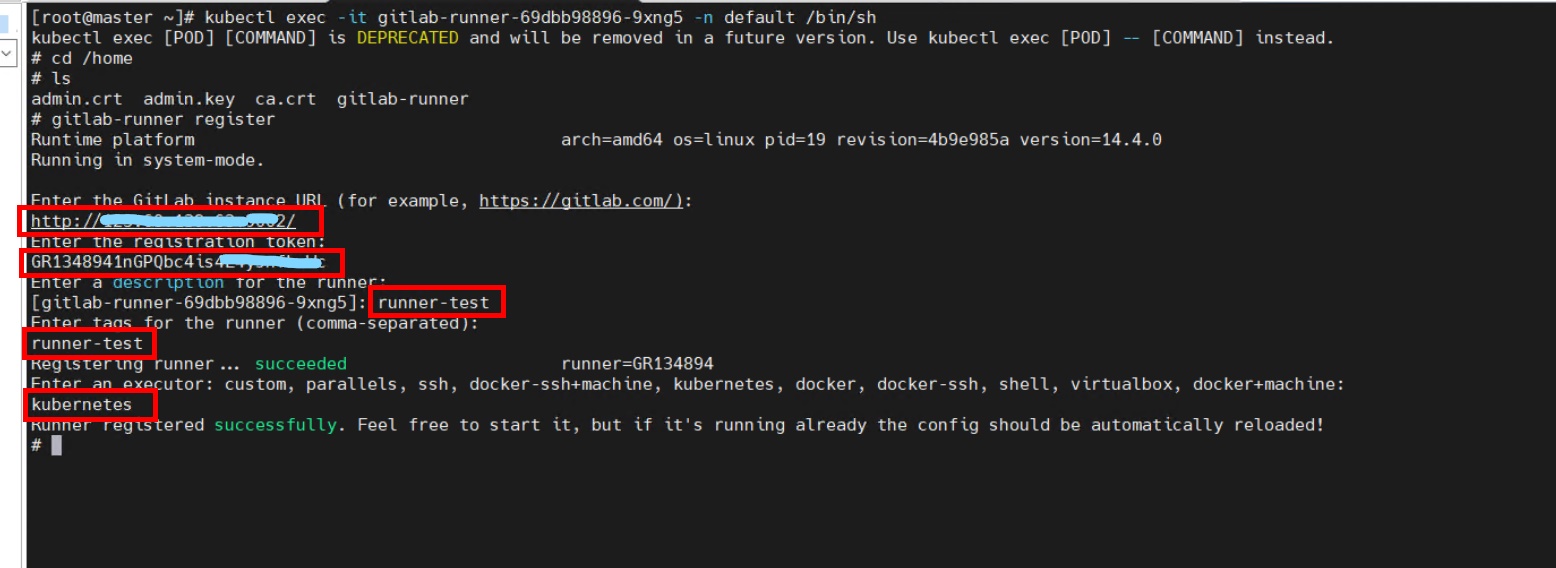
Registering the GitLab Runner
Perform registration in the GitLab Runner container. Currently, interactive registration is used. Obtain the registration information from GitLab. Choose GitLab > Group runners > Settings > CI/CD > Runners.
Upload the prepared gitlab-runner-helper image to the private image repository in advance, go to the GitLab Runner container, and modify the configuration file.
# cd /etc/gitlab-runner
# mkdir kubessl
# cp /home/admin.crt /etc/gitlab-runner/kubessl
# cp /home/ca.crt /etc/gitlab-runner/kubessl
# cp /home/admin.key /etc/gitlab-runner/kubessl
# vim /etc/gitlab-runner/config.toml
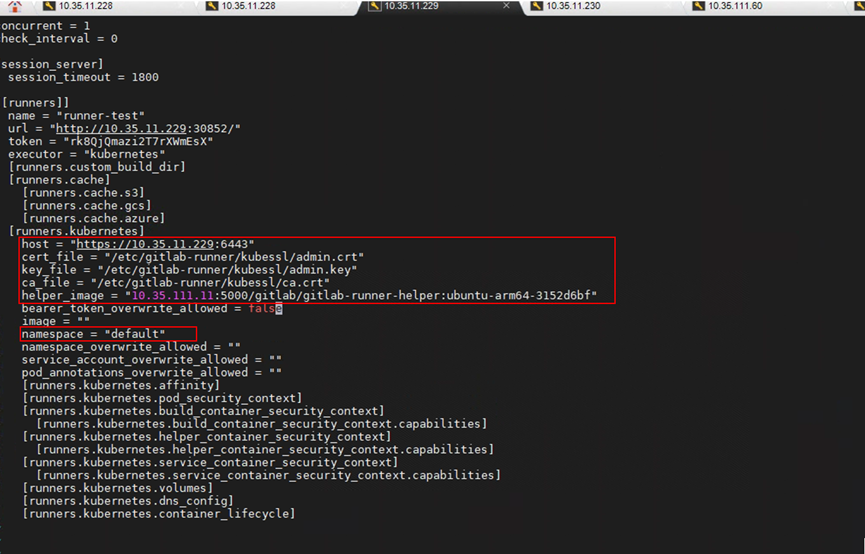
Adding the DNS Record of the GitLab Container to the Manager Node
View the IP address of the GitLab container.
# kubectl get pods –AowideAdd the IP address of the GitLab container to the Kubernetes DNS configuration file.
# kubectl edit configmaps coredns -n kube-system
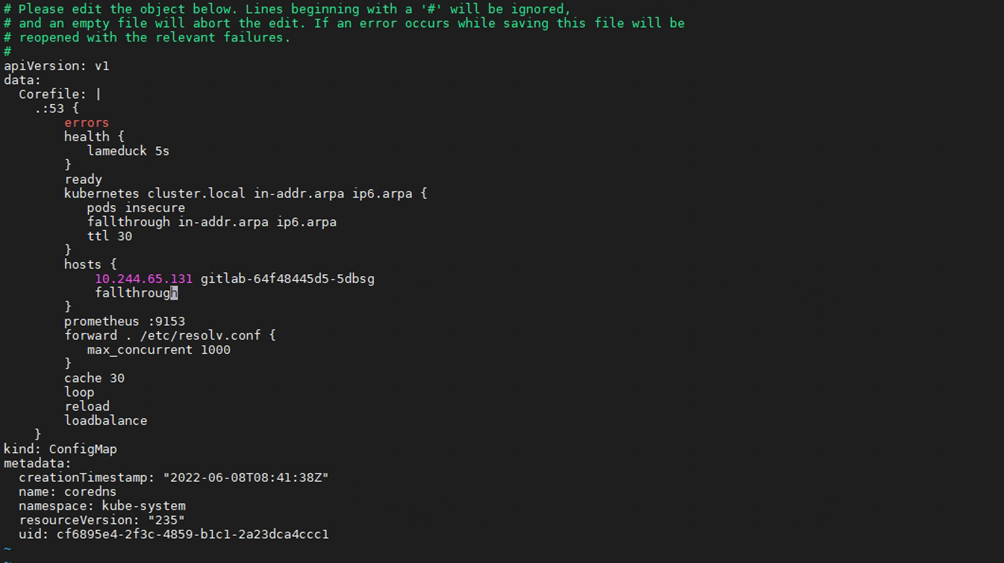
Restart the CoreDNS service.
# kubectl scale deployment coredns -n kube-system --replicas=0 # kubectl scale deployment coredns -n kube-system --replicas=2
GitLab Running Testing
Return to the GitLab web IDE and choose CI/CD > Editor > Create new CI/CD pipeline.
- Compile the YAML file as follows:
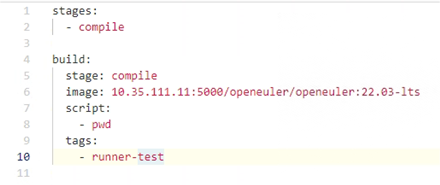
- Choose Pipelines and view the status.










