Introduction to secGear
Overview
With the rapid development of cloud computing, more and more enterprises deploy computing services on the cloud. The security of user data on the third-party cloud infrastructure is facing great challenges. Confidential computing is a technology that uses hardware-based trusted execution environments (TEEs) to protect confidentiality and integrity of data in use. It relies on the bottom-layer hardware to build the minimum trust dependency, which removes the OS, hypervisor, infrastructure, system administrator, and service provider from the trusted entity list as unauthorized entities to reduce potential risks. There are various confidential computing technologies (such as Intel SGX, Arm TrustZone, and RSIC-V Keystone) and software development kits (SDKs) in the industry and the application ecosystem of different TEEs are isolated from each other, which brings high development and maintenance costs to confidential computing application developers. To help developers quickly build confidential computing solutions that protect data security on the cloud, openEuler launches the unified confidential computing programming framework secGear.
Architecture
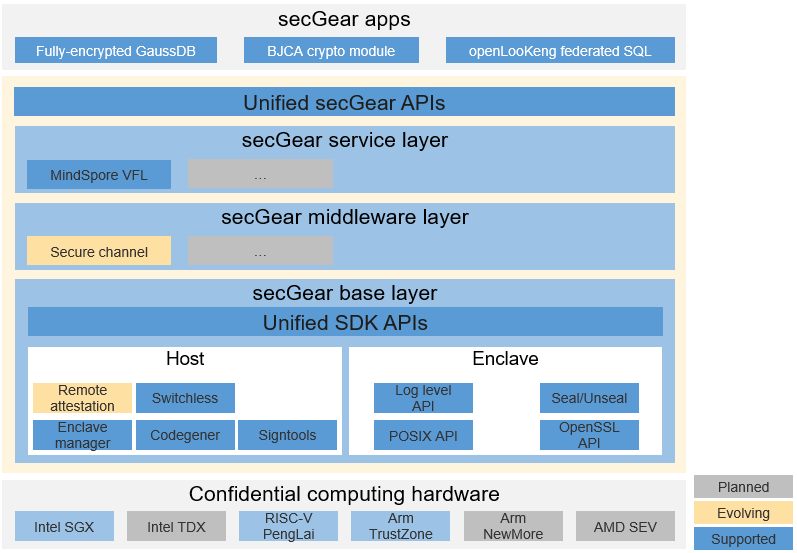
secGear features the following benefits:
- Architecture compatibility: It masks differences between different SDK APIs by sharing the same set of source code across multiple architectures.
- Easy development: The development tools and common security components allow users to focus on services, significantly improving development efficiency.
- High performance: The switchless feature improves the interaction performance between the rich execution environment (REE) and TEE by more than 10-fold in typical scenarios such as frequent interactions between the REE and TEE and big data interaction.
Key Features
Switchless
Pain Points
After a conventional application is reconstructed using confidential computing, the rich execution environment (REE) logic frequently invokes the TEE logic or the REE frequently exchanges large data blocks with the TEE. Each call between the REE and TEE requires context switching among the REE user mode, REE kernel mode, driver, TEE kernel mode, and TEE user mode. When large blocks of data are exchanged during the call, multiple memory copies are generated. In addition, the interaction performance between the REE and TEE deteriorates due to factors such as the size limit of underlying data blocks, which severely affects the implementation of confidential computing applications.
Solution
Switchless is a technology that uses shared memory to reduce the number of context switches and data copies between the REE and TEE to optimize the interaction performance.
Remote Attestation
Pain Points
Confidential computing is developed to ensure data security on the cloud. However, due to the damage of data leakage, tenants still have concerns about the theoretical security of confidential computing, which affects its promotion and application.
Solution
Confidential computing vendors have launched the remote attestation technology, which enables tenants to detect the trustworthiness status of the TEE and TAs on the cloud at any time. Remote attestation is a real-time measurement technology that measures the TEE and applications running in the TEE, generates attestation reports, and uses the preset root key to sign the reports to prevent them from being tampered with or forged. secGear encapsulates remote attestation APIs based on the remote attestation capability of each vendor's SDK. secGear must run on the Kunpeng platform.
Secure Channel
Pain Points
When requesting the confidential computing service on the cloud, the data owner needs to upload the data to be processed to the TEE on the cloud for processing. Because the TEE is not connected to the network, the data needs to be transferred to the REE over the network in plaintext and then transferred to the TEE from the REE. The data plaintext is exposed in the REE memory, which poses security risks.
Solution
A secure channel is a technology that combines confidential computing remote attestation to implement secure key negotiation between the data owner and the TEE on the cloud. It negotiates a sessionkey owned only by the data owner and the TEE on the cloud. Then the sessionkey is used to encrypt user data transferred over the network. After receiving the ciphertext data, the REE transfers the data to the TEE for decryption and processing.
Acronyms and Abbreviations
| Acronym/Abbreviation | Full Name |
|---|---|
| REE | rich execution environment |
| TEE | trusted execution environment |
| EDL | enclave description language |










