utsudo User Guide
This document describes how to install and use utsudo. utsudo is fully compatible with sudo in terms of parameter functions and plug-in usage, greatly reducing users' learning costs.
This document is intended for utsudo developers, testers, and common users.
utsudo Introduction
The utsudo project was initiated in June 2022. It aims to reconstruct sudo using the Rust language. utsudo is an efficient, secure, and flexible privilege escalation tool. The modules of utsudo include the common tool library, overall framework, and plug-in functions.
utsudo Installation
In version 0.0.4, some files of utsudo conflict with those of sudo. Therefore, you need to use yumdownloader to download the binary RPM package of utsudo, and then run rpm to install the package with conflicts allowed.
Run yumdownloader utsudo to download the utsudo binary RPM package.
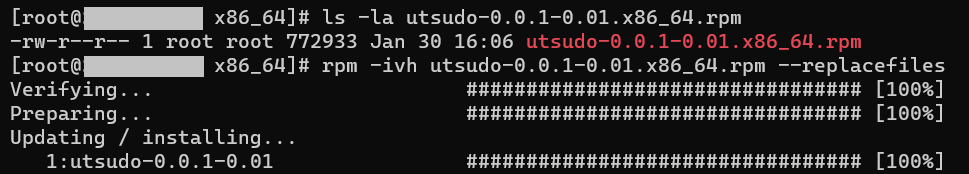
Then, run sudo rpm -ivh utsudo-0.0.1-0.04.x86_64.rpm --replacefiles to install utsudo. The execution process is as follows.
After the installation is complete, run rpm -qa | grep utsudo to check whether utsudo is properly installed, as shown in the following figure.

As shown in the preceding figure, utsudo has been installed and the version is 0.0.1-0.04.
utsudo will be continuously updated in the future.
utsudo Usage
utsudo has various options. Some options are as follows. You can run utsudo -h for details.
-e, --edit Edit a file instead of running a command.
-k, --reset-timestamp Invalidate the timestamp file.
-l, --list List user privileges or check a specific command. Use the option twice for the longer format.
-e
The -e option is used to edit files.
utsudo -e is equivalent to sudoedit. When the command is executed, a common user is used to edit a file. A file in the writable directory of the calling user cannot be edited unless the user is root.
In a directory on which the current user does not have write permission, a file test.txt exists on which the current user does not have write permission. When you edit the test.txt file as a common user, a message is displayed indicating that you do not have the permission. You can run utsudo -e to edit the file. The following figure shows the execution process.

As shown in the figure, the content of the test.txt file is successfully modified. (utsudo -e is okay!! was added in the editor.)
-k
The -k option invalidates the timestamp.
By default, you need to enter the password when you run the utsudo command for the first time and every five minutes. The -k parameter forces the user to enter the password the next time the utsudo command is executed.

By default, you do not need to enter the password for five minutes after running utsudo for the first time.
However, as shown in the figure, the utsudo -k command invalidates the timestamp of the utsudo command.
-l
The -l option displays the commands that the current user can execute by using utsudo.
The execution process is as follows:

As shown in the figure, the test user can run the following commands:
(ALL) ALL
That is, all commands can be executed by user test, indicating that the /etc/sudoers file does not restrict the user.
This section briefly describes how to use utsudo. Other functions and options of utsudo are not listed.










