Secure Boot
Overview
Secure Boot relies on public and private key pairs to sign and verify components in the booting process. During booting, the previous component authenticates the digital signature of the next component. If the authentication is successful, the next component runs. If the authentication fails, the booting stops. Secure Boot ensures the integrity of each component during system booting and prevents unauthenticated components from being loaded and running, preventing security threats to the system and user data.
Components to be authenticated and loaded in sequence in Secure Boot are BIOS, shim, GRUB, and vmlinuz (kernel image).
Related EFI startup components are signed by the openEuler signature platform using signcode. The public key certificate is integrated into the signature database by the BIOS. During the boot, the BIOS verifies the shim. The shim and GRUB components obtain the public key certificate from the signature database of the BIOS and verify the next-level components.
Background and Solutions
In earlier openEuler versions, secure boot components are not signed. Therefore, the secure boot function cannot be directly used to ensure the integrity of system components.
In openEuler 22.03 LTS SP3 and later versions, openEuler uses the community signature platform to sign OS components, including the GRUB and vmlinuz components, and integrates the community signature root certificate in the shim component.
For the shim component, to facilitate end-to-end secure boot, the signature platform of the openEuler community is used for signature. After external CAs officially operate the secure boot component signature service, the signatures of these CAs will be integrated into the shim module of openEuler.
Usage
Obtaining the openEuler Certificate
To obtain the openEuler root certificate, visit https://www.openeuler.org/en/security/security-bulletins and download it from the Certificate Center directory.
The root certificate name on the web page are openEuler Shim Default CA and default-x509ca.cert.
Operation in the BIOS
Import the openEuler root certificate to the certificate database of the BIOS and enable secure boot in the BIOS.
For details about how to import the BIOS certificate and enable secure boot, see the documents provided by the BIOS vendor.
Operation in the OS
Check the certificate information in the database: mokutil –db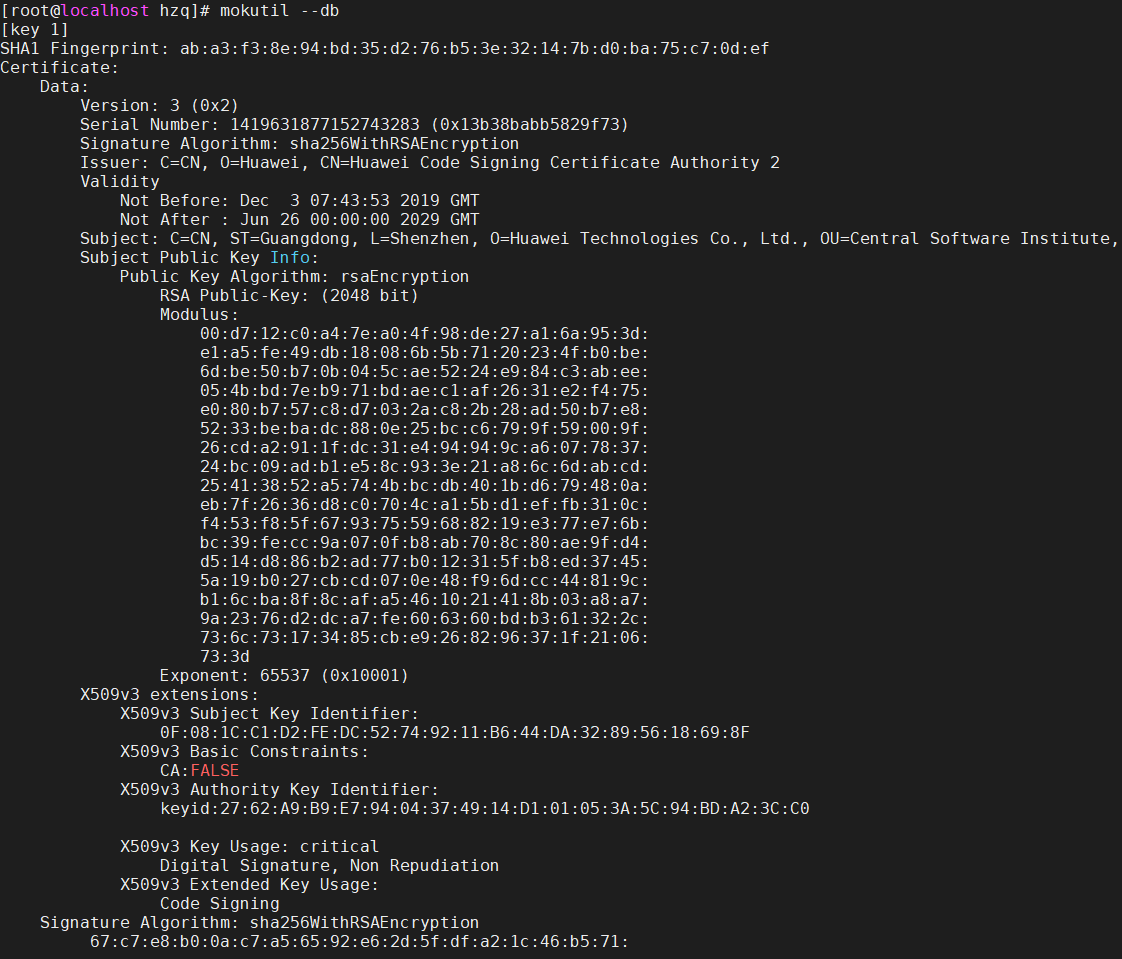 Note: There is a large amount of certificate information. Only some important information is displayed in the screenshot.
Note: There is a large amount of certificate information. Only some important information is displayed in the screenshot.
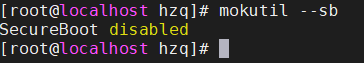
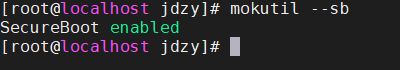
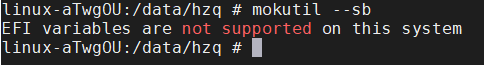
Check the secure boot status: mokutil --sb
- SecureBoot disabled: Secure boot is disabled.
- SecureBoot enabled: Secure boot is enabled.
- not supported: The system does not support secure boot.
Constraints
- Software: The OS must be booted in UEFI mode.
- Architecture: Arm or x86
- Hardware: The BIOS must support the verification function related to secure boot.










