Dynamic Integrity Measurement (DIM)
This section describes the DIM feature and its usage.
Context
With the development of the IT industry, information systems are facing an increasing number of security risks. Information systems run a large amount of software, some of which is inevitably vulnerable. Once exploited by attackers, these vulnerabilities could severely damage system services, resulting in data leakage and service unavailability.
Most software attacks are accompanied by integrity damage, such as malicious process execution, configuration file tampering, and backdoor implantation. Therefore, protection technologies are proposed in the industry. Key data is measured and verified during system startup to ensure that the system can run properly. However, popular integrity protection technologies (such as secure boot and file integrity measurement) cannot protect memory data during process running. If an attacker somehow modifies the instructions of a process, the process may be hijacked or implanted with a backdoor, which is highly destructive and stealthy. To defend against such attacks, the DIM technology is proposed to measure and protect key data in the memory of a running process.
Terminology
Static baseline: baseline measurement data generated by parsing the binary file of the measurement target
Dynamic baseline: result of the first measurement on the measurement target
Measurement policy: configuration information for measuring the target
Measurement log: list of measurement information, including the measurement targets and measurement results
Description
The DIM feature measures key data (such as code sections and data sections) in the memory during program running and compares the measurement result with the baseline value to determine whether the memory data has been tampered with. In this way, DIM can detect attacks and take countermeasures.
Function Scope
- Currently, DIM supports only AArch64 and x86 architectures.
- Currently, DIM supports measurement of the following key memory data:
- Code section of a user-mode process (the section whose attribute is PT_LOAD and permission is RX in the ELF file, and the virtual memory area whose permission is RX after the corresponding process is loaded)
- Kernel module code section, whose start address and length are core_layout.base and core_layout.text_size respectively in the struct module structure corresponding to the kernel module.
- Kernel code section, corresponding to _stext to _etext (Addresses that may change due to the kernel static key mechanism are skipped.)
- DIM can work with the following hardware:
- The measurement result can be extended to the Platform Configuration Register (PCR) of Trusted Platform Module (TPM) 2.0 to connect to the remote attestation service.
Technical Limitations
- For user-mode processes, only mapped code sections of files can be measured. Anonymous code sections cannot be measured.
- Kernel hot patches cannot be measured.
- Measurement can only be triggered proactively. If a file is attacked and recovered during two measurement processes, the attack cannot be identified.
- Proactive modification of code sections, such as relocation of code sections, self-modification, and hot patches, will be identified as attacks.
- For kernel and kernel module measurement, the measurement result when dynamic baseline establishment is triggered is used as the measurement baseline value. The static baseline value only serves as a fixed identifier.
- The measurement target must have been loaded to the memory when dynamic baseline establishment is triggered (for example, process running or kernel module loading). Otherwise, the object cannot be measured.
- If the TPM PCR needs to be used to verify measurement logs, the DIM module cannot be removed. Otherwise, the measurement logs will be cleared and cannot match the PCR.
NOTE
After DIM is enabled, system performance is affected in the following aspects:
- Loading the DIM feature and managing baseline data and measurement logs consume system memory. The impact depends on the protection policy configuration.
- Hashing is performed during DIM running, which consumes CPU resources. The impact depends on the size of the data to be measured.
- Resources will be locked and semaphores need to be obtained during DIM running, which may cause other concurrent processes to wait.
Specification Constraints
| Item | Value |
|---|---|
| Maximum size of a policy file, static baseline file, signature file, or certificate file | 10MB |
| Maximum number of tampering measurement logs recorded for a measurement target during multiple measurement periods after a dynamic baseline is established. | 10 |
| Maximum number of measurement policies that can be stored in /etc/dim/policy | 10,000 |
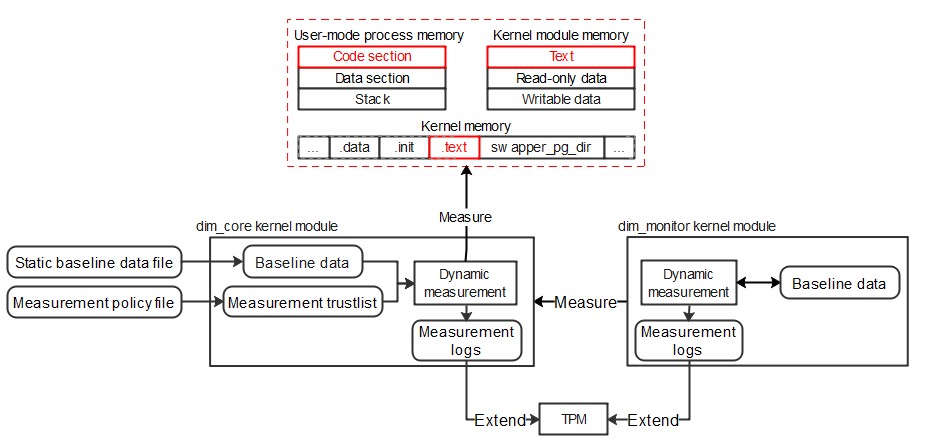
Architecture Description
DIM includes the dim_tools and dim software packages, which contain the following components:
| Software Package | Component | Description |
|---|---|---|
| dim_tools | dim_gen_baseline | User-mode component for generating the static baseline, which is required for generating the dynamic measurement. The baseline data is imported when DIM runs. |
| dim | dim_core | Kernel module for executing the core dynamic measurement logic, including policy parsing, static baseline parsing, dynamic baseline establishment, measurement execution, measurement logging, and TPM extension operations, to measure key memory data. |
| dim | dim_monitor | Kernel module for measuring and protecting dim_core code sections and key data to prevent DIM function failures caused by attacks on dim_core. |
The following figure shows the overall architecture:
Key Procedures
Both the dim_core and dim_monitor modules provide the memory data measurement function, including the following core processes:
- Dynamic baseline process: The dim_core module reads and parses the policy and static baseline file, measures the code section of the target process, stores the measurement result as a dynamic baseline in the memory, compares the dynamic baseline data with the static baseline data, and records the comparison result in measurement logs. The dim_monitor module measures the code sections and key data of the dim_core module, uses the data as the dynamic baseline, and records measurement logs.
- Dynamic measurement process: The dim_core and dim_monitor modules measure the target and compare the measurement result with the dynamic baseline. If the measurement result is inconsistent with the dynamic baseline, the dim_core and dim_monitor modules record the result in measurement logs.
Interfaces
Interface Files
| Path | Description |
|---|---|
| /etc/dim/policy | Measurement policy file |
| /etc/dim/policy.sig | Measurement policy signature file, which is used to store the signature information of the policy file and is used when the signature verification function is enabled |
| /etc/dim/digest_list/*.hash | Static baseline file, which is used to store measurement baseline values |
| /etc/dim/digest_list/*.hash.sig | Static baseline signature file, which is used to store the signature information of the static baseline file and is used when the signature verification function is enabled |
| /etc/keys/x509_dim.der | Certificate file, which is used to verify the signature information of the policy file and static baseline file and is used when the signature verification function is enabled |
| /sys/kernel/security/dim | DIM file system directory, which is generated after the DIM kernel module is loaded and provides kernel interfaces for operating the DIM function |
File Formats
Measurement policy file format
The lines, each representing a measurement policy, are in plaintext and are separated by Unix newline (LF) characters. The following configuration formats are supported:
User-mode process code section measurement
textmeasure obj=BPRM_TEXT path=<absolute path of the binary file corresponding to the executable file or dynamic library of the measurement target process>Kernel module code section measurement
textmeasure obj=MODULE_TEXT name=<kernel module name>Kernel measurement
textmeasure obj=KERNEL_TEXT
Example:
shell# cat /etc/dim/policy measure obj=BPRM_TEXT path=/usr/bin/bash measure obj=BPRM_TEXT path=/usr/lib64/libc.so.6 measure obj=MODULE_TEXT name=ext4 measure obj=KERNEL_TEXTStatic baseline file format
The lines, each representing a static baseline, are in plaintext and are separated by Unix newline (LF) characters. The following configuration formats are supported:
User-mode process baseline
textdim USER sha256:6ae347be2d1ba03bf71d33c888a5c1b95262597fbc8d00ae484040408a605d2b <absolute path of the binary file corresponding to the executable file or dynamic library of the measurement target process>Kernel module baseline
textdim KERNEL sha256:a18bb578ff0b6043ec5c2b9b4f1c5fa6a70d05f8310a663ba40bb6e898007ac5 <kernel release number>/<kernel module name>Kernel baseline
textdim KERNEL sha256:2ce2bc5d65e112ba691c6ab46d622fac1b7dbe45b77106631120dcc5441a3b9a <kernel release number>
Example:
textdim USER sha256:6ae347be2d1ba03bf71d33c888a5c1b95262597fbc8d00ae484040408a605d2b /usr/bin/bash dim USER sha256:bc937f83dee4018f56cc823f5dafd0dfedc7b9872aa4568dc6fbe404594dc4d0 /usr/lib64/libc.so.6 dim KERNEL sha256:a18bb578ff0b6043ec5c2b9b4f1c5fa6a70d05f8310a663ba40bb6e898007ac5 6.4.0-1.0.1.4.oe2309.x86_64/dim_monitor dim KERNEL sha256:2ce2bc5d65e112ba691c6ab46d622fac1b7dbe45b77106631120dcc5441a3b9a 6.4.0-1.0.1.4.oe2309.x86_64Measurement log format
The lines, each representing a measurement log, are in plaintext and are separated by Unix newline (LF) characters. The format is as follows:
text<PCR number> <measurement log hash> <measurement algorithm>:<measurement hash> <measurement target> <measurement log type>Example:
The code section of the bash process is measured. The measurement result is consistent with the static baseline.
text12 0f384a6d24e121daf06532f808df624d5ffc061e20166976e89a7bb24158eb87 sha256:db032449f9e20ba37e0ec4a506d664f24f496bce95f2ed972419397951a3792e /usr/bin.bash [static baseline]The code section of the bash process is measured. The measurement result is inconsistent with the static baseline.
text12 0f384a6d24e121daf06532f808df624d5ffc061e20166976e89a7bb24158eb87 sha256:db032449f9e20ba37e0ec4a506d664f24f496bce95f2ed972419397951a3792e /usr/bin.bash [tampered]The code section of the ext4 kernel module is measured. No static baseline is found.
text12 0f384a6d24e121daf06532f808df624d5ffc061e20166976e89a7bb24158eb87 sha256:db032449f9e20ba37e0ec4a506d664f24f496bce95f2ed972419397951a3792e ext4 [no static baseline]dim_monitor measures dim_core and records the measurement result of the baseline.
text12 660d594ba050c3ec9a7cdc8cf226c5213c1e6eec50ba3ff51ff76e4273b3335a sha256:bdab94a05cc9f3ad36d29ebbd14aba8f6fd87c22ae580670d18154b684de366c dim_core.text [dynamic baseline] 12 28a3cefc364c46caffca71e7c88d42cf3735516dec32796e4883edcf1241a7ea sha256:0dfd9656d6ecdadc8ec054a66e9ff0c746d946d67d932cd1cdb69780ccad6fb2 dim_core.data [dynamic baseline]
Certificate and signature file formats
The files are in the common format. For details, see Enabling Signature Verification.
Kernel Module Parameters
dim_core parameters
Parameter Description Value Range Default Value measure_log_capacity Maximum number of measurement logs recorded by dim_core. When this value is reached, dim_core stops recording measurement logs. 100-UINT_MAX (64-bit OS) 100000 measure_schedule Scheduling time after a process or module is measured, in milliseconds. The value 0 indicates that measurement is not scheduled. 0-1000 0 measure_interval Automatic measurement interval, in minutes. The value 0 indicates that automatic measurement is not enabled. 0-525600 0 measure_hash Measurement hash algorithm sha256, sm3 sha256 measure_pcr The TPM PCR to which the measurement result is extended. The value 0 indicates that the measurement result is not extended. The value must be an actual TPM PCR number. 0-128 0 signature Whether to enable the policy file and signature verification. The value 0 indicates that they are disabled, and the value 1 indicates that they are enabled. 0, 1 0 Example:
shellinsmod /path/to/dim_core.ko measure_log_capacity=10000 measure_schedule=10 measure_pcr=12 modprobe dim_core measure_log_capacity=10000 measure_schedule=10 measure_pcr=12dim_monitor parameters
Parameter Description Value Range Default Value measure_log_capacity Maximum number of measurement logs recorded by dim_monitor. When this value is reached, dim_monitor stops recording measurement logs. 100-UINT_MAX (64-bit OS) 100000 measure_hash Measurement hash algorithm sha256, sm3 sha256 measure_pcr The TPM PCR to which the measurement result is extended. The value 0 indicates that the measurement result is not extended. 0-128 0 Example:
shellinsmod /path/to/dim_monitor.ko measure_log_capacity=10000 measure_hash=sm3 modprobe dim_monitor measure_log_capacity=10000 measure_hash=sm3
Kernel Interfaces
dim_core interface
Interface Attribute Function Example measure Write-only Write 1 to trigger dynamic measurement. If the operation is successful, 0 is returned. If the operation fails, an error code is returned. echo 1 > /sys/kernel/security/dim/measure baseline_init Write-only Write 1 to trigger dynamic baseline establishment. If the operation is successful, 0 is returned. If the operation fails, an error code is returned. echo 1 > /sys/kernel/security/dim/baseline_init ascii_runtime_measurements Read-only Read the interface to query measurement logs. cat /sys/kernel/security/dim/ascii_runtime_measurements runtime_status Read-only Read the interface to query the status information. If the operation fails, an error code is returned. cat /sys/kernel/security/dim/runtime_status interval Read/Write Write a numeric string to set the automatic measurement interval (the value range is the same as that of measure_interval). Read the interface to query the current automatic measurement interval. If the query fails, an error code is returned. echo 10 > /sys/kernel/security/dim/interval
cat /sys/kernel/security/dim/intervaldim_core Statuses
The possible statuses of dim_core are as follows:
- DIM_NO_BASELINE: dim_core is loaded but no operation is performed.
- DIM_BASELINE_RUNNING: The dynamic baseline is being established.
- DIM_MEASURE_RUNNING: Dynamic measurement is being performed.
- DIM_PROTECTED: The dynamic baseline has been established and is protected.
- DIM_ERROR: An error occurs during dynamic baseline establishment or dynamic measurement. You need to rectify the error and trigger dynamic baseline establishment or dynamic measurement again.
dim_monitor interfaces
Interface Attribute Description Example monitor_run Write-only Write 1 to trigger measurement. If the operation is successful, 0 is returned. If the operation fails, an error code is returned. echo 1 > /sys/kernel/security/dim/monitor_run monitor_baseline Write-only Write 1 to trigger baseline establishment. If the operation is successful, 0 is returned. If the operation fails, an error code is returned. echo 1 > /sys/kernel/security/dim/monitor_baseline monitor_ascii_runtime_measurements Read-only Read the interface to query measurement logs. cat /sys/kernel/security/dim/monitor_ascii_runtime_measurements monitor_status Read-only Read the interface to query the status information. If the operation fails, an error code is returned. cat /sys/kernel/security/dim/monitor_status dim_monitor Statuses
- ready: dim_monitor is loaded but no operation is performed.
- running: The dynamic baseline is being established or dynamic measurement is being performed.
- error: An error occurs during dynamic baseline establishment or dynamic measurement. You need to rectify the error and trigger dynamic baseline establishment or dynamic measurement again.
- protected: The dynamic baseline has been established and is protected.
User-Mode Tool Interface
See https://atomgit.com/openeuler/dim_tools/blob/master/doc/cmd.md for the details of the dim_gen_baseline CLI interface.
Usage
Installing and Uninstalling DIM
Prerequisites:
- OS: openEuler 23.09 or later
- Kernel: openEuler kernel 5.10 or 6.4
Install dim_tools and dim software packages. The following uses openEuler 23.09 as an example:
# yum install -y dim_tools dimAfter the software packages are installed, the DIM kernel components are not loaded by default. You can run the following commands to load or unload them:
# modprobe dim_core or insmod /path/to/dim_core.ko
# modprobe dim_monitor or insmod /path/to/dim_monitor.ko
# rmmod dim_monitor
# rmmod dim_coreAfter the components are loaded successfully, you can run the following commands to query the components:
# lsmod | grep dim_core
dim_core 77824 1 dim_monitor
# lsmod | grep dim_monitor
dim_monitor 36864 0Unload the KO files before uninstalling the RPM package.
# rmmod dim_monitor
# rmmod dim_core
# rpm -e dimNOTE
dim_monitor must be loaded after dim_core and removed before dim_core. You can also install DIM from source. For details, see https://atomgit.com/openeuler/dim/blob/master/README.md.
Measuring Code Sections of User-Mode Processes
Prerequisites:
The dim_core module is loaded successfully.
A user-mode resident measurement target program has been prepared. This section uses /opt/dim/demo/dim_test_demo as an example.
shell# /opt/dim/demo/dim_test_demo &
Step 1: Generate a static baseline for the binary file corresponding to the measurement target process.
# mkdir -p /etc/dim/digest_list
# dim_gen_baseline /opt/dim/demo/dim_test_demo -o /etc/dim/digest_list/test.hashStep 2: Configure a measurement policy.
# echo "measure obj=BPRM_TEXT path=/opt/dim/demo/dim_test_demo" > /etc/dim/policyStep 3: Trigger dynamic baseline establishment.
# echo 1 > /sys/kernel/security/dim/baseline_initStep 4: Query measurement logs.
# cat /sys/kernel/security/dim/ascii_runtime_measurements
0 e9a79e25f091e03a8b3972b1a0e4ae2ccaed1f5652857fe3b4dc947801a6913e sha256:02e28dff9997e1d81fb806ee5b784fd853eac8812059c4dba7c119c5e5076989 /opt/dim/demo/dim_test_demo [static baseline]If the preceding measurement log is displayed, the target process is measured successfully and the measurement result is consistent with the static baseline.
Step 5: Trigger dynamic measurement.
# echo 1 > /sys/kernel/security/dim/measureAfter the measurement is complete, you can perform Step 4 to query the measurement logs. If the measurement result is consistent with the dynamic baseline, the measurement logs are not updated. Otherwise, an exception measurement log is added. If an attacker attempts to tamper with the target program (for example, by modifying and recompiling the code) and restart the target program, for example:
# pkill dim_test_demo
# /opt/dim/demo/dim_test_demo &Trigger the measurement again and query the measurement logs. You can see a measurement log marked with "tampered."
# echo 1 > /sys/kernel/security/dim/measure
# cat /sys/kernel/security/dim/ascii_runtime_measurements
0 e9a79e25f091e03a8b3972b1a0e4ae2ccaed1f5652857fe3b4dc947801a6913e sha256:02e28dff9997e1d81fb806ee5b784fd853eac8812059c4dba7c119c5e5076989 /opt/dim/demo/dim_test_demo [static baseline]
0 08a2f6f2922ad3d1cf376ae05cf0cc507c2f5a1c605adf445506bc84826531d6 sha256:855ec9a890ff22034f7e13b78c2089e28e8d217491665b39203b50ab47b111c8 /opt/dim/demo/dim_test_demo [tampered]Measuring Code Sections of Kernel Modules
Prerequisites:
The dim_core module is loaded successfully.
A measurement target kernel module has been prepared. This section uses dim_test_module as an example, whose path is /opt/dim/demo/dim_test_module.ko.
shell# insmod /opt/dim/demo/dim_test_module.ko
NOTE
The kernel version of the environment where the module is compiled must be the same as the current kernel version. Run the following command to confirm:
# modinfo dim_monitor.ko | grep vermagic | grep "$(uname -r)"
vermagic: 6.4.0-1.0.1.4.oe2309.x86_64 SMP preempt mod_unload modversionsThe first field of the vermagic kernel module information must be the same as the current kernel version.
Step 1: Generate a static baseline for the measurement target kernel module.
# mkdir -p /etc/dim/digest_list
# dim_gen_baseline /opt/dim/demo/dim_test_module.ko -o /etc/dim/digest_list/test.hashStep 2: Configure a measurement policy.
# echo "measure obj=MODULE_TEXT name=dim_test_module" > /etc/dim/policyStep 3: Trigger dynamic baseline establishment.
# echo 1 > /sys/kernel/security/dim/baseline_initStep 4: Query measurement logs.
# cat /sys/kernel/security/dim/ascii_runtime_measurements
0 9603a9d5f87851c8eb7d2619f7abbe28cb8a91f9c83f5ea59f036794e23d1558 sha256:9da4bccc7ae1b709deab8f583b244822d52f3552c93f70534932ae21fac931c6 dim_test_module [static baseline]The preceding measurement log indicates that dim_test_module is successfully measured and the current measurement result is used as the baseline value for subsequent measurement. The hash value in the measurement log is not the actual measurement value.
Step 5: Trigger dynamic measurement.
echo 1 > /sys/kernel/security/dim/measureAfter the measurement is complete, you can perform Step 4 to query the measurement logs. If the measurement result is consistent with the dynamic baseline, the measurement logs are not updated. Otherwise, an exception measurement log is added. If an attacker attempts to tamper with the target kernel module (for example, by modifying and recompiling the code) and reload the module, for example:
rmmod dim_test_module
insmod /opt/dim/demo/dim_test_module.koTrigger the measurement again and query the measurement logs. You can see a measurement log marked with "tampered."
# cat /sys/kernel/security/dim/ascii_runtime_measurements
0 9603a9d5f87851c8eb7d2619f7abbe28cb8a91f9c83f5ea59f036794e23d1558 sha256:9da4bccc7ae1b709deab8f583b244822d52f3552c93f70534932ae21fac931c6 dim_test_module [static baseline]
0 6205915fe63a7042788c919d4f0ff04cc5170647d7053a1fe67f6c0943cd1f40 sha256:4cb77370787323140cb572a789703be1a4168359716a01bf745aa05de68a14e3 dim_test_module [tampered]Measuring Code Sections of the Kernel
Prerequisites:
- The dim_core module is loaded successfully.
Step 1: generate a static baseline for the kernel.
# mkdir -p /etc/dim/digest_list
# dim_gen_baseline -k "$(uname -r)" -o /etc/dim/digest_list/test.hash /boot/vmlinuz-6.4.0-1.0.1.4.oe2309.x86_64NOTE
The file name /boot/vmlinuz-6.4.0-1.0.1.4.oe2309.x86_64 is used as an example.
Step 2: Configure a DIM policy.
# echo "measure obj=KERNEL_TEXT" > /etc/dim/policyStep 3: Trigger dynamic baseline establishment.
# echo 1 > /sys/kernel/security/dim/baseline_initStep 4: Query measurement logs.
# cat /sys/kernel/security/dim/ascii_runtime_measurements
0 ef82c39d767dece1f5c52b31d1e8c7d55541bae68a97542dda61b0c0c01af4d2 sha256:5f1586e95b102cd9b9f7df3585fe13a1306cbd464f2ebe47a51ad34128f5d0af 6.4.0-1.0.1.4.oe2309.x86_64 [static baseline]The preceding measurement log indicates that the kernel is successfully measured and the current measurement result is used as the baseline value for subsequent measurement. The hash value in the measurement log is not the actual measurement value.
Step 5: Trigger dynamic measurement.
# echo 1 > /sys/kernel/security/dim/measureAfter the measurement is complete, you can perform Step 4 to query the measurement logs. If the measurement result is consistent with the dynamic baseline, the measurement logs are not updated. Otherwise, an exception measurement log is added.
Measuring the dim_core Module
Prerequisites:
- The dim_core and dim_monitor modules are loaded successfully.
- The measurement policy has been configured.
Step 1: Trigger dynamic baseline establishment for dim_core.
# echo 1 > /sys/kernel/security/dim/baseline_initStep2: Trigger dynamic baseline establishment for dim_monitor.
# echo 1 > /sys/kernel/security/dim/monitor_baselineStep 3: Query dim_monitor measurement logs.
# cat /sys/kernel/security/dim/monitor_ascii_runtime_measurements
0 c1b0d9909ddb00633fc6bbe7e457b46b57e165166b8422e81014bdd3e6862899 sha256:35494ed41109ebc9bf9bf7b1c190b7e890e2f7ce62ca1920397cd2c02a057796 dim_core.text [dynamic baseline]
0 9be7121cd2c215d454db2a8aead36b03d2ed94fad0fbaacfbca83d57a410674f sha256:f35d20aae19ada5e633d2fde6e93133c3b6ae9f494ef354ebe5b162398e4d7fa dim_core.data [dynamic baseline]The preceding measurement log indicates that dim_core is successfully measured and the current measurement result is used as the baseline value for subsequent measurement.
NOTE
If you skip dynamic baseline establishment and directly perform measurement, "tampered" is displayed in the log.
Step 4: Trigger dynamic measurement of dim_monitor.
# echo 1 > /sys/kernel/security/dim/monitor_runIf the measurement result is consistent with the dynamic baseline, the measurement logs are not updated. Otherwise, an exception measurement log is added. If dynamic baseline establishment for dim_core is triggered again after the policy is modified, the measurement target changes, and the baseline data managed by dim_core also changes. As a result, the dim_monitor measurement result changes.
# echo "measure obj=BPRM_TEXT path=/usr/bin/bash" > /etc/dim/policy
# echo 1 > /sys/kernel/security/dim/baseline_initTrigger the measurement of dim_monitor again and query the measurement logs. You can see a measurement log marked with "tampered."
# echo 1 > /sys/kernel/security/dim/monitor_run
# cat /sys/kernel/security/dim/monitor_ascii_runtime_measurements
0 c1b0d9909ddb00633fc6bbe7e457b46b57e165166b8422e81014bdd3e6862899 sha256:35494ed41109ebc9bf9bf7b1c190b7e890e2f7ce62ca1920397cd2c02a057796 dim_core.text [dynamic baseline]
0 9be7121cd2c215d454db2a8aead36b03d2ed94fad0fbaacfbca83d57a410674f sha256:f35d20aae19ada5e633d2fde6e93133c3b6ae9f494ef354ebe5b162398e4d7fa dim_core.data [dynamic baseline]
0 6a60d78230954aba2e6ea6a6b20a7b803d7adb405acbb49b297c003366cfec0d sha256:449ba11b0bfc6146d4479edea2b691aa37c0c025a733e167fd97e77bbb4b9dab dim_core.data [tampered]Extending to the TPM PCR
Prerequisites:
The TPM 2.0 has been installed in the system. After the following command is executed, the command output is not empty:
shell# ls /dev/tpm* /dev/tpm0 /dev/tpmrm0The tpm2-tools software package has been installed in the system. After the following command is executed, the command output is not empty:
shell# rpm -qa tpm2-toolsThe measurement policy and static baseline have been configured.
Step 1: Load the dim_core and dim_monitor modules and set the numbers of the PCRs to which the measurement results are extended. In this example, PCR 12 is specified for the dim_core measurement result, and PCR 13 is specified for the dim_monitor measurement result.
# modprobe dim_core measure_pcr=12
# modprobe dim_monitor measure_pcr=13Step 2: Trigger baseline establishment for dim_core and dim_monitor.
# echo 1 > /sys/kernel/security/dim/baseline_init
# echo 1 > /sys/kernel/security/dim/monitor_baselineStep 3: Check the measurement logs. Each log is marked with the corresponding TPM PCR number.
# cat /sys/kernel/security/dim/ascii_runtime_measurements
12 2649c414d1f9fcac1c8d0df8ae7b1c18b5ea10a162b957839bdb8f8415ec6146 sha256:83110ce600e744982d3676202576d8b94cea016a088f99617767ddbd66da1164 /usr/lib/systemd/systemd [static baseline]
# cat /sys/kernel/security/dim/monitor_ascii_runtime_measurements
13 72ee3061d5a80eb8547cd80c73a80c3a8dc3b3e9f7e5baa10f709350b3058063 sha256:5562ed25fcdf557efe8077e231399bcfbcf0160d726201ac8edf7a2ca7c55ad0 dim_core.text [dynamic baseline]
13 8ba44d557a9855c03bc243a8ba2d553347a52c1a322ea9cf8d3d1e0c8f0e2656 sha256:5279eadc235d80bf66ba652b5d0a2c7afd253ebaf1d03e6e24b87b7f7e94fa02 dim_core.data [dynamic baseline]Step 4: Check the TPM PCRs. Extended values have been written to the corresponding PCRs.
# tpm2_pcrread sha256 | grep "12:"
12: 0xF358AC6F815BB29D53356DA2B4578B4EE26EB9274E553689094208E444D5D9A2
# tpm2_pcrread sha256 | grep "13:"
13: 0xBFB9FF69493DEF9C50E52E38B332BDA8DE9C53E90FB96D14CD299E756205F8EAEnabling Signature Verification
Prerequisites:
A public key certificate and a signature private key have been prepared. The signature algorithm is RSA, the hash algorithm is sha256, and the certificate format is DER. You can also run the following commands to generate the files:
shell# openssl genrsa -out dim.key 4096 # openssl req -new -sha256 -key dim.key -out dim.csr -subj "/C=AA/ST=BB/O=CC/OU=DD/CN=DIM Test" # openssl x509 -req -days 3650 -signkey dim.key -in dim.csr -out dim.crt # openssl x509 -in dim.crt -out dim.der -outform DERThe measurement policy has been configured.
Step 1: Save the DER certificate as /etc/keys/x509_dim.der.
# mkdir -p /etc/keys
# cp dim.der /etc/keys/x509_dim.derStep 2: Sign the policy file and static baseline file. The signature file name must be the original file name suffixed with .sig.
# openssl dgst -sha256 -out /etc/dim/policy.sig -sign dim.key /etc/dim/policy
# openssl dgst -sha256 -out /etc/dim/digest_list/test.hash.sig -sign dim.key /etc/dim/digest_list/test.hashStep 3: Load the dim_core module and enable the signature verification function.
modprobe dim_core signature=1Now, the policy file and static baseline file can be loaded only after they pass the signature verification. The baseline establishment will fail if it is triggered after the policy file is modified:
# echo "" >> /etc/dim/policy
# echo 1 > /sys/kernel/security/dim/baseline_init
-bash: echo: write error: Key was rejected by serviceNOTE
If the signature verification of a static baseline file fails, dim_core skips the parsing of the file without causing a baseline establishment failure.
Configuring Measurement Algorithms
Prerequisites:
- The measurement policy has been configured.
Step 1: Load the dim_core and dim_monitor modules and configure the measurement algorithm. The following uses the SM3 algorithm as an example.
# modprobe dim_core measure_hash=sm3
# modprobe dim_monitor measure_hash=sm3Step 2: Configure a policy that establishes a static baseline of the SM3 algorithm for the measurement target program.
# echo "measure obj=BPRM_TEXT path=/opt/dim/demo/dim_test_demo" > /etc/dim/policy
# dim_gen_baseline -a sm3 /opt/dim/demo/dim_test_demo -o /etc/dim/digest_list/test.hashStep 3: Trigger baseline establishment.
# echo 1 > /sys/kernel/security/dim/baseline_init
# echo 1 > /sys/kernel/security/dim/monitor_baselineStep 4: Check the measurement logs. Each log is marked with the corresponding hash algorithm.
# cat /sys/kernel/security/dim/ascii_runtime_measurements
0 585a64feea8dd1ec415d4e67c33633b97abb9f88e6732c8a039064351d24eed6 sm3:ca84504c02bef360ec77f3280552c006ce387ebb09b49b316d1a0b7f43039142 /opt/dim/demo/dim_test_demo [static baseline]
# cat /sys/kernel/security/dim/monitor_ascii_runtime_measurements
0 e6a40553499d4cbf0501f32cabcad8d872416ca12855a389215b2509af76e60b sm3:47a1dae98182e9d7fa489671f20c3542e0e154d3ce941440cdd4a1e4eee8f39f dim_core.text [dynamic baseline]
0 2c862bb477b342e9ac7d4dd03b6e6705c19e0835efc15da38aafba110b41b3d1 sm3:a4d31d5f4d5f08458717b520941c2aefa0b72dc8640a33ee30c26a9dab74eae9 dim_core.data [dynamic baseline]Configuring Automatic Measurement
Prerequisites:
- The measurement policy has been configured.
Method 1: Load the dim_core module and set the automatic measurement interval to 1 minute.
modprobe dim_core measure_interval=1After the module is loaded, dynamic baseline establishment is automatically triggered. Then, dynamic measurement is triggered every minute.
NOTE
In this case, do not configure the measurement policy for dim_core to measure its own code sections. Otherwise, false alarms may occur. In addition, you need to configure /etc/dim/policy in advance. Otherwise, the module fails to be loaded when measure_interval is set to 1.
Method 2: After the dim_core module is loaded, you can configure the measurement interval through the kernel module interface. In the following example, the measurement interval is set to 1 minute.
modprobe dim_core
echo 1 > /sys/kernel/security/dim/intervalIn this case, the measurement is not triggered immediately. One minute later, dynamic baseline establishment, or dynamic measurement, is triggered. Subsequently, dynamic measurement is triggered every minute.
Configuring the Measurement Scheduling Time
Prerequisites:
- The measurement policy has been configured.
Load the dim_core module and set the measurement scheduling time to 10 ms.
modprobe dim_core measure_schedule=10When the dynamic baseline establishment or dynamic measurement is triggered, dim_core schedules the CPU to release 10 ms each time a process is measured.