Trusted Computing
Trusted Computing Basics
What Is Trusted Computing
The definition of being trusted varies with international organizations.
Trusted Computing Group (TCG):
An entity that is trusted always achieves the desired goal in an expected way.
International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) (1999):
The components, operations, or processes involved in computing are predictable under any conditions and are resistant to viruses and a certain degree of physical interference.
IEEE Computer Society Technical Committee on Dependable Computing:
Being trusted means that the services provided by the computer system can be proved to be reliable, and mainly refers to the reliability and availability of the system.
In short, being trusted means that the system operates according to a pre-determined design and policy.
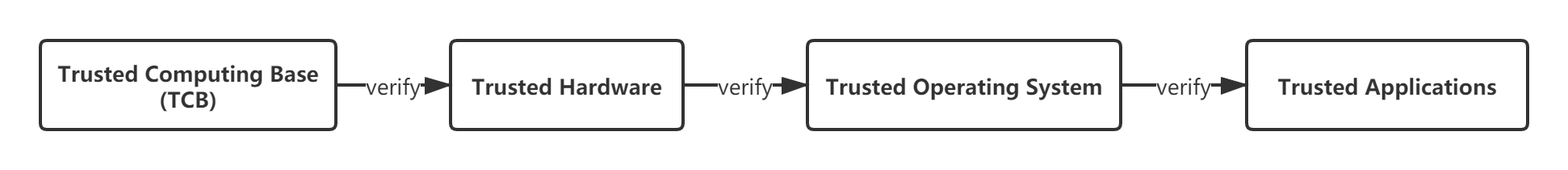
A trusted computing system consists of a root of trust, a trusted hardware platform, operating system (OS), and application. The basic idea of the system is to create a trusted computing base (TCB) first, and then establish a trust chain that covers the hardware platform, OS, and application. In the trust chain, authentication is performed from the root to the next level, extending trust level by level and building a secure and trusted computing environment.
Unlike traditional security approaches that reactively tackle threats—such as identifying and removing viruses individually—trusted computing employs an allowlist strategy. This ensures that only verified kernels, kernel modules, and applications can operate on the system. Any program that is modified or unrecognized is automatically blocked from execution.