DNF Plugin Command Usage
Install the DNF plugin:
dnf install dnf-hotpatch-pluginAfter installing the plugin, you can run DNF commands to use plugin functions related to hot patches, such as hot patch scanning (dnf hot-updateinfo), setting and querying (dnf hotpatch), and applying (dnf hotupgrade). This document describes the usage of the commands.
Hot Patch Scanning
hot-updateinfo can scan hot patches and query hot patches for specified CVEs.
$ dnf hot-updateinfo list cves [--cve [cve_id]]
General DNF options:
-h, --help, --help-cmd
show command help
--cve CVES, --cves CVES
Include packages needed to fix the given CVE, in updates--list
Query the CVEs on the host that can be fixed and their related cold and hot patches.
shell$ dnf hot-updateinfo list cves # cve-id level cold-patch hot-patch Last metadata expiration check: 0:54:46 ago on Thu Mar 16 09:40:27 2023. CVE-2022-3080 Important/Sec. bind-libs-9.16.23-10.oe2203.aarch64 patch-bind-libs-9.16.23-09-name-1-111.aarch64 CVE-2021-25220 Moderate/Sec. bind-9.16.23-10.oe2203.aarch64 - CVE-2022-1886 Critical/Sec. vim-common-8.2-39.oe2203.aarch64 patch-vim-common-8.2-38-name-1-233.aarch64 CVE-2022-1725 Low/Sec. vim-minimal-8.2-58.oe2203.aarch64 patch-vim-minimal-8.2-57-name-2-11.aarch64Query cold and hot patches for specified CVEs.
shell$ dnf hot-updateinfo list cves --cve CVE-2022-3080 # cve-id level cold-patch hot-patch Last metadata expiration check: 0:54:46 ago on Thu Mar 16 09:40:27 2023. CVE-2022-3080 Important/Sec. bind-libs-9.16.23-10.oe2203.aarch64 patch-bind-libs-9.16.23-09-name-1-111.aarch64An empty list will be displayed if the CVE does not exist.
shell$ dnf hot-updateinfo list cves --cve CVE-2022-3089 # cve-id level cold-patch hot-patch Last metadata expiration check: 0:54:46 ago on Thu Mar 16 09:40:27 2023.
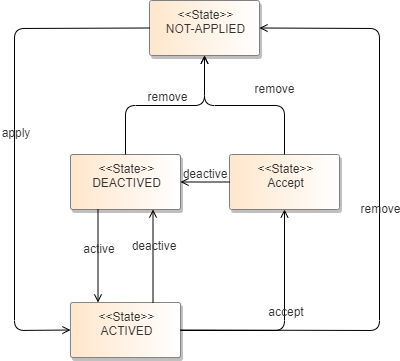
Hot Patch Statuses
A hot patch can be in the following statuses:
NOT-APPLIED: The hot patch is not installed.
DEACTIVED: The hot patch is installed.
ACTIVED: The hot patch is activated.
ACCEPT: The hot patch has been accepted and will be applied after a reboot.
Querying and Changing Hot Patch Statuses
hotpatch can be used to query and convert hot patch statuses.
$ dnf hotpatch
General DNF options:
-h, --help, --help-cmd
show command help
--cve CVES, --cves CVES
Include packages needed to fix the given CVE, in updates
Hotpatch command-specific options:
--list [{cve, cves}] show list of hotpatch
--apply APPLY_NAME apply hotpatch
--remove REMOVE_NAME remove hotpatch
--active ACTIVE_NAME active hotpatch
--deactive DEACTIVE_NAME
deactive hotpatch
--accept ACCEPT_NAME accept hotpatchdnf hotpatch --listlists available hot patches in the system.shell$ dnf hotpatch --list Last metadata expiration check: 0:54:46 ago on Thu Mar 16 09:40:27 2023. base-pkg/hotpatch status redis-6.2.5-1/HP001 NOT-APPLIED redis-6.2.5-1/HP001 NOT-APPLIED redis-6.2.5-1/HP002 ACTIVED redis-6.2.5-1/HP002 ACTIVEDdnf hotpatch --list cvesqueries hot patches related to CVEs.shell$ dnf hotpatch --list cves Last metadata expiration check: 0:54:46 ago on Thu Mar 16 09:40:27 2023. CVE-id base-pkg/hotpatch status CVE-2023-1111 redis-6.2.5-1/HP001 NOT-APPLIED CVE-2023-1112 redis-6.2.5-1/HP001 NOT-APPLIED CVE-2023-2221 redis-6.2.5-1/HP002 ACTIVED CVE-2023-2222 redis-6.2.5-1/HP002 ACTIVEDdnf hotpatch --list cves --cve <CVE-id>queries hot patches for specified CVEs.shell$ dnf hotpatch --list cves --cve CVE-2023-1111 Last metadata expiration check: 0:54:46 ago on Thu Mar 16 09:40:27 2023. CVE-id base-pkg/hotpatch status CVE-2023-1111 redis-6.2.5-1/HP001 NOT-APPLIEDAn empty list will be displayed if the specified CVE does not exist when running
dnf hotpatch --list cves --cve <CVE-id>.shell$ dnf hotpatch --list cves --cve CVE-2023-1 Last metadata expiration check: 0:54:46 ago on Thu Mar 16 09:40:27 2023.dnf hotpatch --apply <patch name>applies a hot patch. You can runsyscare listto query the hot patch status after applying the hot patch. For details about hot patch statuses, see the previous section.shell$ dnf hotpatch --apply redis-6.2.5-1/HP2 Last metadata expiration check: 2:38:51 ago on Thu May 25 13:49:28 2023. Gonna apply this hot patch: redis-6.2.5-1/HP2 apply hot patch 'redis-6.2.5-1/HP2' succeed $ syscare list Uuid Name Status 25209ddc-b1e4-48e0-b715-e759ec8db401 redis-6.2.5-1/HP2 ACTIVEDdnf hotpatch --deactive <patch name>deactivates a hot patch. You can runsyscare listto query the hot patch status after deactivating the hot patch. For details about hot patch statuses, see the previous section.shell$ dnf hotpatch --deactive redis-6.2.5-1/HP2 Last metadata expiration check: 2:39:10 ago on Thu May 25 13:49:28 2023. Gonna deactive this hot patch: redis-6.2.5-1/HP2 deactive hot patch 'redis-6.2.5-1/HP2' succeed $ syscare list Uuid Name Status 25209ddc-b1e4-48e0-b715-e759ec8db401 redis-6.2.5-1/HP2 DEACTIVEDdnf hotpatch --remove <patch name>removes a hot patch. You can runsyscare listto query the hot patch status after removing the hot patch. For details about hot patch statuses, see the previous section.shell$ dnf hotpatch --remove redis-6.2.5-1/HP2 Last metadata expiration check: 2:53:25 ago on Thu May 25 13:49:28 2023. Gonna remove this hot patch: redis-6.2.5-1/HP2 remove hot patch 'redis-6.2.5-1/HP2' succeed $ syscare list Uuid Name Status 25209ddc-b1e4-48e0-b715-e759ec8db401 redis-6.2.5-1/HP2 NOT-APPLIEDdnf hotpatch --active <patch name>activating a hot patch.You can runsyscare listto query the hot patch status after activating the hot patch. For details about hot patch statuses, see the previous section.shell$ dnf hotpatch --active redis-6.2.5-1/HP2 Last metadata expiration check: 2:53:37 ago on Thu May 25 13:49:28 2023. Gonna active this hot patch: redis-6.2.5-1/HP2 active hot patch 'redis-6.2.5-1/HP2' failed, remain original status. $ syscare list Uuid Name Status 25209ddc-b1e4-48e0-b715-e759ec8db401 redis-6.2.5-1/HP2 ACTIVEDdnf hotpatch --accept <patch name>accepts a hot patch. You can runsyscare listto query the hot patch status after accepting the hot patch. For details about hot patch statuses, see the previous section.shell$ dnf hotpatch --accept redis-6.2.5-1/HP2 Last metadata expiration check: 2:53:25 ago on Thu May 25 13:49:28 2023. Gonna accept this hot patch: redis-6.2.5-1/HP2 remove hot patch 'redis-6.2.5-1/HP2' succeed $ syscare list Uuid Name Status 25209ddc-b1e4-48e0-b715-e759ec8db401 redis-6.2.5-1/HP2 ACCEPTED
Applying Hot Patches
The hotupgrade command is used to apply hot patches to fix specified or all CVEs.
$ dnf hotupgrade [--cve [cve_id]] [SPEC ...]
General DNF options:
-h, --help, --help-cmd
show command help
--cve CVES, --cves CVES
Include packages needed to fix the given CVE, in updates
command-specific options:
SPEC Hotpatch specification- Case 1: If hot patches have been installed,
dnf hotupgradeapplies all available hot patches.
$ dnf hotupgrade
Last metadata expiration check: 4:04:34 ago on Fri Jun 02 06:33:41 2023.
Gonna apply these hot patches:['patch-redis-6.2.5-1-HP001-1-1.x86_64', 'patch-redis-6.2.5-1-HP002-1-1.x86_64']
The target package 'redis-6.2.5-1' has a hotpatch 'HP001' applied
Gonna remove these hot patches: ['redis-6.2.5-1/HP001']
Remove hot patch redis-6.2.5-1/HP001.
Package patch-redis-6.2.5-1-HP001-1-1.x86_64 is already installed.
Package patch-redis-6.2.5-1-HP002-1-1.x86_64 is already installed.
Dependencies resolved.
Nothing to do.
Complete!
Applying hot patch
Apply hot patch succeed: redis-6.2.5-1/HP001.
Apply hot patch failed: redis-6.2.5-1/HP002.- Case 2: If hot patches have not been installed,
dnf hotupgradeinstalls and applies all available hot patches.
$ dnf hotupgrade
Last metadata expiration check: 4:13:16 ago on Fri Jun 02 06:33:41 2023.
Gonna apply these hot patches:['patch-redis-6.2.5-1-HP002-1-1.x86_64', 'patch-redis-6.2.5-1-HP001-1-1.x86_64']
Package patch-redis-6.2.5-1-HP002-1-1.x86_64 is already installed.
Dependencies resolved.
xxxx(Install messages)
Is this ok [y/N]: y
Downloading Packages:
xxxx(Install process)
Complete!
Applying hot patch
Apply hot patch succeed: redis-6.2.5-1/HP001.- Case 3:
dnf hotupgrade <patch_name>upgrades specified hot patches.
$ dnf hotupgrade patch-redis-6.2.5-1-HP001-1-1.x86_64
Last metadata expiration check: 0:07:49 ago on Thu Jun 08 12:03:46 2023.
Package patch-redis-6.2.5-1-HP001-1-1.x86_64 is already installed.
Dependencies resolved.
Nothing to do.
Complete!
Applying hot patch
Apply hot patch succeed: redis-6.2.5-1/HP001.--cve- Case 1:
dnf hotupgrade --cve <cve_id>is used to install and apply a hot patch for a specified CVE.
shell$ dnf hotupgrade --cve CVE-2021-11 Last metadata expiration check: xxx Dependencies resolved. xxxx(Install messages) Is this ok [y/N]: y Downloading Packages: xxxx(Install process) Complete! Applying hot patch Apply hot patch succeed: redis-6.2.5-1/HP001- Case 2:
dnf hotupgrade --cve <cve_id>is used for a CVE that does not exist.
shell$ dnf hotupgrade --cve CVE-2021-11 Last metadata expiration check: xxx The cve doesnt exist: CVE-2021-11 Error: No hot patches marked for install.- Case 3:
dnf hotupgrade --cve <cve_id>is used to install and apply a hot patch of a higher version for a CVE that has a hot patch of a lower version. The hot patch of the lower version is uninstalled.
shell$ dnf hotupgrade --cve CVE-2021-22 Last metadata expiration check: xxx The target package 'redis-6.2.5-1' has a hotpatch 'HP001' applied Gonna remove these hot patches: ['redis-6.2.5-1/HP001'] Is this ok [y/N]: y Remove hot patch redis-6.2.5-1/HP001 xxxx (install messages and process install) Apply hot patch apply hot patch succeed: redis-6.2.5-1/HP002- Case 4:
dnf hotupgrade --cve <cve_id>is used to install and apply a hot patch for a CVE that has the latest hot patch.
shell$ dnf hotupgrade --cve CVE-2021-22 Package patch -redis-6.2.5-1-HP002-1-1.x86_64 is already installed. Dependencies resolved. Nothing to do. Complete! Applying hot patch Apply hot patch succeed: redis-6.2.5-1/HP002- Case 1:
SPECshelldnf hotupgrade bind-libs-hotpatch
The output of this sub-command is the same as that of --cve.
Usage Example
Assume that the repositories of hot and cold patches on this host have been enabled.
Scan CVEs that can be fixed on the host.
$ dnf hot-updateinfo list cves
Last metadata expiration check: 0:00:38 ago on Sat Mar 25 11:53:46 2023.
CVE-2023-22995 Important/Sec. python3-perf-5.10.0-136.22.0.98.oe2203sp1.x86_64 -
CVE-2023-26545 Important/Sec. python3-perf-5.10.0-136.22.0.98.oe2203sp1.x86_64 -
CVE-2022-40897 Important/Sec. python3-setuptools-59.4.0-5.oe2203sp1.noarch -
CVE-2021-1 Important/Sec. redis-6.2.5-2.x86_64 patch-redis-6.2.5-1-HP001-1-1.x86_64
CVE-2021-11 Important/Sec. redis-6.2.5-2.x86_64 patch-redis-6.2.5-1-HP001-1-1.x86_64
CVE-2021-2 Important/Sec. redis-6.2.5-3.x86_64 patch-redis-6.2.5-1-HP002-1-1.x86_64
CVE-2021-22 Important/Sec. redis-6.2.5-3.x86_64 patch-redis-6.2.5-1-HP002-1-1.x86_64
CVE-2021-33 Important/Sec. redis-6.2.5-4.x86_64 -
CVE-2021-3 Important/Sec. redis-6.2.5-4.x86_64 -
CVE-2022-38023 Important/Sec. samba-client-4.17.2-5.oe2203sp1.x86_64 -
CVE-2022-37966 Important/Sec. samba-client-4.17.2-5.oe2203sp1.x86_64 -CVE-2021-1, CVE-2021-11, CVE-2021-2, and CVE-2021-22 can be fixed by hot patches.
Start the Redis service based on the redis.conf configuration file.
$ sudo redis-server ./redis.conf &
[1] 285075
285076:C 25 Mar 2023 12:09:51.503 # oO0OoO0OoO0Oo Redis is starting oO0OoO0OoO0Oo
285076:C 25 Mar 2023 12:09:51.503 # Redis version=255.255.255, bits=64, commit=00000000, modified=0, pid=285076, just started
285076:C 25 Mar 2023 12:09:51.503 # Configuration loaded
285076:M 25 Mar 2023 12:09:51.504 * Increased maximum number of open files to 10032 (it was originally set to 1024).
285076:M 25 Mar 2023 12:09:51.504 * monotonic clock: POSIX clock_gettime
_._
_.-``__ ''-._
_.-`` `. `_. ''-._ Redis 255.255.255 (00000000/0) 64 bit
.-`` .-```. ```\/ _.,_ ''-._
( ' , .-` | `, ) Running in standalone mode
|`-._`-...-` __...-.``-._|'` _.-'| Port: 6380
| `-._ `._ / _.-' | PID: 285076
`-._ `-._ `-./ _.-' _.-'
|`-._`-._ `-.__.-' _.-'_.-'|
| `-._`-._ _.-'_.-' | https://redis.io
`-._ `-._`-.__.-'_.-' _.-'
|`-._`-._ `-.__.-' _.-'_.-'|
| `-._`-._ _.-'_.-' |
`-._ `-._`-.__.-'_.-' _.-'
`-._ `-.__.-' _.-'
`-._ _.-'
`-.__.-'
285076:M 25 Mar 2023 12:09:51.505 # Server initialized
285076:M 25 Mar 2023 12:09:51.505 # WARNING overcommit_memory is set to 0! Background save may fail under low memory condition. To fix this issue add 'vm.overcommit_memory = 1' to /etc/sysctl.conf and then reboot or run the command 'sysctl vm.overcommit_memory=1' for this to take effect.
285076:M 25 Mar 2023 12:09:51.506 * Ready to accept connectionsTest the function before applying the hot patch.
$ telnet 127.0.0.1 6380
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
*100
-ERR Protocol error: expected '$', got ' '
Connection closed by foreign host.Specify CVE-2021-1 and ensure that the related hot patch is associated and applied.
$ dnf hotupgrade --cve CVE-2021-1
Last metadata expiration check: 0:05:19 ago on Sat Mar 25 11:53:46 2023.
Package patch-redis-6.2.5-1-HP001-1-1.x86_64 is already installed.
Dependencies resolved.
Nothing to do.
Complete!
Applying hot patch
Apply hot patch succeed: redis-6.2.5-1/HP001.Run syscare to check whether the hot patch has been applied (the status is ACTIVED).
$ syscare list
Uuid Name Status
cf47649c-b370-4f5a-a914-d2ca4d8f1f3a redis-6.2.5-1/HP001 ACTIVEDCheck whether the CVE has been fixed. Because the patch-redis-6.2.5-1-HP001-1-1.x86_64 hot patch also fixes CVE-2021-11, CVE-2021-1 and CVE-2021-11 no longer exists.
$ dnf hot-updateinfo list cves
Last metadata expiration check: 0:08:48 ago on Sat Mar 25 11:53:46 2023.
CVE-2023-22995 Important/Sec. python3-perf-5.10.0-136.22.0.98.oe2203sp1.x86_64 -
CVE-2023-1076 Important/Sec. python3-perf-5.10.0-136.22.0.98.oe2203sp1.x86_64 -
CVE-2023-26607 Important/Sec. python3-perf-5.10.0-136.22.0.98.oe2203sp1.x86_64 -
CVE-2022-40897 Important/Sec. python3-setuptools-59.4.0-5.oe2203sp1.noarch -
CVE-2021-22 Important/Sec. redis-6.2.5-3.x86_64 patch-redis-6.2.5-1-HP002-1-1.x86_64
CVE-2021-2 Important/Sec. redis-6.2.5-3.x86_64 patch-redis-6.2.5-1-HP002-1-1.x86_64
CVE-2021-33 Important/Sec. redis-6.2.5-4.x86_64 -
CVE-2021-3 Important/Sec. redis-6.2.5-4.x86_64 -
CVE-2022-38023 Important/Sec. samba-client-4.17.2-5.oe2203sp1.x86_64 -
CVE-2022-37966 Important/Sec. samba-client-4.17.2-5.oe2203sp1.x86_64 -Test the function after applying the hot patch.
$ telnet 127.0.0.1 6380
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
*100
-ERR Protocol error: unauthenticated multibulk length
Connection closed by foreign host.Run syscare and specify the patch name to manually remove the hot patch.
$ syscare remove redis-6.2.5-1/HP001
$ syscare list
Uuid Name Status
cf47649c-b370-4f5a-a914-d2ca4d8f1f3a redis-6.2.5-1/HP001 NOT-APPLIEDScan the CVEs to be fixed on the host. CVE-2021-1 and CVE-2021-11 are displayed.
$ dnf hot-updateinfo list cves
Last metadata expiration check: 0:00:38 ago on Sat Mar 25 11:53:46 2023.
CVE-2023-22995 Important/Sec. python3-perf-5.10.0-136.22.0.98.oe2203sp1.x86_64 -
CVE-2023-26545 Important/Sec. python3-perf-5.10.0-136.22.0.98.oe2203sp1.x86_64 -
CVE-2022-40897 Important/Sec. python3-setuptools-59.4.0-5.oe2203sp1.noarch -
CVE-2021-1 Important/Sec. redis-6.2.5-2.x86_64 patch-redis-6.2.5-1-HP001-1-1.x86_64
CVE-2021-11 Important/Sec. redis-6.2.5-2.x86_64 patch-redis-6.2.5-1-HP001-1-1.x86_64
CVE-2021-2 Important/Sec. redis-6.2.5-3.x86_64 patch-redis-6.2.5-1-HP002-1-1.x86_64
CVE-2021-22 Important/Sec. redis-6.2.5-3.x86_64 patch-redis-6.2.5-1-HP002-1-1.x86_64
CVE-2021-33 Important/Sec. redis-6.2.5-4.x86_64 -
CVE-2021-3 Important/Sec. redis-6.2.5-4.x86_64 -
CVE-2022-38023 Important/Sec. samba-client-4.17.2-5.oe2203sp1.x86_64 -
CVE-2022-37966 Important/Sec. samba-client-4.17.2-5.oe2203sp1.x86_64 -- Case 1
Apply hot patch patch-redis-6.2.5-1-HP002-1-1.x86_64.
$ dnf hotupgrade patch-redis-6.2.5-1-HP002-1-1.x86_64
Last metadata expiration check: 0:05:19 ago on Sat Mar 25 11:53:46 2023.
Package patch-redis-6.2.5-1-HP002-1-1.x86_64 is already installed.
Dependencies resolved.
Nothing to do.
Complete!
Applying hot patch
Apply hot patch succeed: redis-6.2.5-1/HP002.Scan the CVEs to be fixed on the host. Because the cold patch redis-6.2.5-3.x86_64 corresponding to patch-redis-6.2.5-1-HP002-1-1.x86_64 is of a higher version than redis-6.2.5-2.x86_64, redis-6.2.5-2.x86_64 also fixes CVE-2021-1, CVE-2021-11, CVE-2021-2, and CVE-2021-22.
$ dnf hot-updateinfo list cves
Last metadata expiration check: 0:00:38 ago on Sat Mar 25 11:53:46 2023.
CVE-2023-22995 Important/Sec. python3-perf-5.10.0-136.22.0.98.oe2203sp1.x86_64 -
CVE-2023-26545 Important/Sec. python3-perf-5.10.0-136.22.0.98.oe2203sp1.x86_64 -
CVE-2022-40897 Important/Sec. python3-setuptools-59.4.0-5.oe2203sp1.noarch -
CVE-2021-33 Important/Sec. redis-6.2.5-4.x86_64 -
CVE-2021-3 Important/Sec. redis-6.2.5-4.x86_64 -
CVE-2022-38023 Important/Sec. samba-client-4.17.2-5.oe2203sp1.x86_64 -
CVE-2022-37966 Important/Sec. samba-client-4.17.2-5.oe2203sp1.x86_64 -- Case 2
Open the xxx-updateinfo.xml.gz file in the repodata directory of the hot patch repository. Check the information related to CVE-2021-33 and CVE-2021-3.
<update from="openeuler.org" type="security" status="stable">
<id>openEuler-SA-2022-3</id>
<title>An update for mariadb is now available for openEuler-22.03-LTS</title>
<severity>Important</severity>
<release>openEuler</release>
<issued date="2022-04-16"></issued>
<references>
<reference href="https://nvd.nist.gov/vuln/detail/CVE-2021-46658" id="CVE-2021-3" title="CVE-2021-3" type="cve"></reference>
<reference href="https://nvd.nist.gov/vuln/detail/CVE-2021-46658" id="CVE-2021-33" title="CVE-2021-33" type="cve"></reference>
</references>
<description>patch-redis-6.2.5-2-HP001.(CVE-2022-24048)</description>
<pkglist>
<hot_patch_collection>
<name>openEuler</name>
<package id="CVE-2021-3" arch="aarch64" name="patch-redis-6.2.5-2-HP001" release="1" version="1">
<filename>patch-redis-6.2.5-2-HP001-1-1.aarch64.rpm</filename>
</package>
<package id="CVE-2021-3" arch="x86_64" name="patch-redis-6.2.5-2-HP001" release="1" version="1">
<filename>patch-redis-6.2.5-2-HP001-1-1.x86_64.rpm</filename>
</package>
</hot_patch_collection>
</pkglist>
</update>The format of the name field of package is patch-<source package name>-<source package version>-<source package release>-<hot patch name>. In the example, patch-redis-6.2.5-2-HP001 requires the source code version of redis-6.2.5-2 to be installed. Check the version of Redis on the host.
$ rpm -qa | grep redis
redis-6.2.5-1.x86_64redis-6.2.5-2 is not installed. Therefore, the hot patch will not be displayed.
$ dnf hot-updateinfo list cves
Last metadata expiration check: 0:00:38 ago on Sat Mar 25 11:53:46 2023.
CVE-2023-22995 Important/Sec. python3-perf-5.10.0-136.22.0.98.oe2203sp1.x86_64 -
CVE-2023-26545 Important/Sec. python3-perf-5.10.0-136.22.0.98.oe2203sp1.x86_64 -
CVE-2022-40897 Important/Sec. python3-setuptools-59.4.0-5.oe2203sp1.noarch -
CVE-2021-33 Important/Sec. redis-6.2.5-4.x86_64 -
CVE-2021-3 Important/Sec. redis-6.2.5-4.x86_64 -
CVE-2022-38023 Important/Sec. samba-client-4.17.2-5.oe2203sp1.x86_64 -
CVE-2022-37966 Important/Sec. samba-client-4.17.2-5.oe2203sp1.x86_64 -